

A roundup of the week’s most important cybersecurity news.
- Hackers breached accounts of developers at the dYdX crypto exchange.
- North Korean hackers used new macOS malware to steal cryptocurrency.
- Malicious AI-themed Chrome extensions were installed by 300,000 users.
- Connecticut residents were charged with stealing $3m.
Hackers breached developer accounts at the dYdX crypto exchange
Attackers compromised accounts of developers at the decentralised crypto exchange dYdX and injected malware into official software packages (npm and PyPI). Researchers at Socket discovered the breach.
The npm and PyPI packages are used by programmers to work with the exchange’s protocols, including creating wallets and executing trades. As billions of dollars flow through dYdX, the threat was severe.
The target was wallet seed phrases. Once a developer interacted with an infected library, the malware copied access keys and sent them to the attackers’ server. The culprits used website addresses that looked almost identical to the exchange’s official domains.
For developers using the Python version, matters were worse: a remote-access trojan was installed. Running in the background every ten seconds, it allowed the attackers to execute arbitrary code on the victim’s machine, enabling the theft of cryptocurrency, passwords and personal files, and monitoring of user activity.
Socket’s specialists noted the intruders understood the system’s internals, hiding malicious code deep within legitimate, automatically executed files.
After the alert, the exchange confirmed the breach and urged anyone who downloaded updates in January 2026 to isolate affected computers immediately and move funds to new, secure wallets.
1/ IMPORTANT SECURITY ANNOUNCEMENT — READ IF YOU HAVE USED VERSIONS OF DYDX-V4 CLIENTS HOSTED ON PyPI or NPM.
— dYdX (@dYdX) January 29, 2026
North Korean hackers used new macOS malware to steal cryptocurrencies
North Korean hackers are running personalised campaigns, using AI-generated videos to deliver malware to crypto users, reported Mandiant experts.
The goal is financial gain, indicated by the toolset used in an attack on an unnamed fintech firm. According to Mandiant, researchers found seven distinct macOS malware families and attributed them to the group UNC1069, tracked since 2018.
The victim was contacted via Telegram from a compromised account of a cryptocurrency company executive. After establishing trust, the hackers sent a Calendly link that redirected to a fake Zoom conference page hosted on attacker infrastructure.
According to the victim, the hackers showed a deepfake video of the crypto firm’s CEO. During the call, the attacker feigned audio issues and, under that pretext, instructed the victim how to “fix the errors” by running commands that kicked off an infection chain for both Windows and macOS.
The hackers then sequentially deployed seven malware families:
- WAVESHAPER — a backdoor running as a background service, collecting system information and loading subsequent modules;
- HYPERCALL — a loader that downloads malicious dynamic libraries and injects them directly into memory;
- HIDDENCALL — a backdoor granting direct keyboard access, command execution and file operations;
- SILENCELIFT — a minimalist backdoor that relays screen-lock status to the attackers’ server and can intercept Telegram messages given root privileges;
- DEEPBREATH — a data-theft tool that bypasses macOS protections and steals Keychain contents, browser data, Telegram data and Apple Notes;
- SUGARLOADER — a loader using an encrypted configuration to fetch next-stage payloads;
- CHROMEPUSH — a browser data-mining tool masquerading as the “Google Docs Offline” extension, intercepting keystrokes and cookies and taking screenshots.
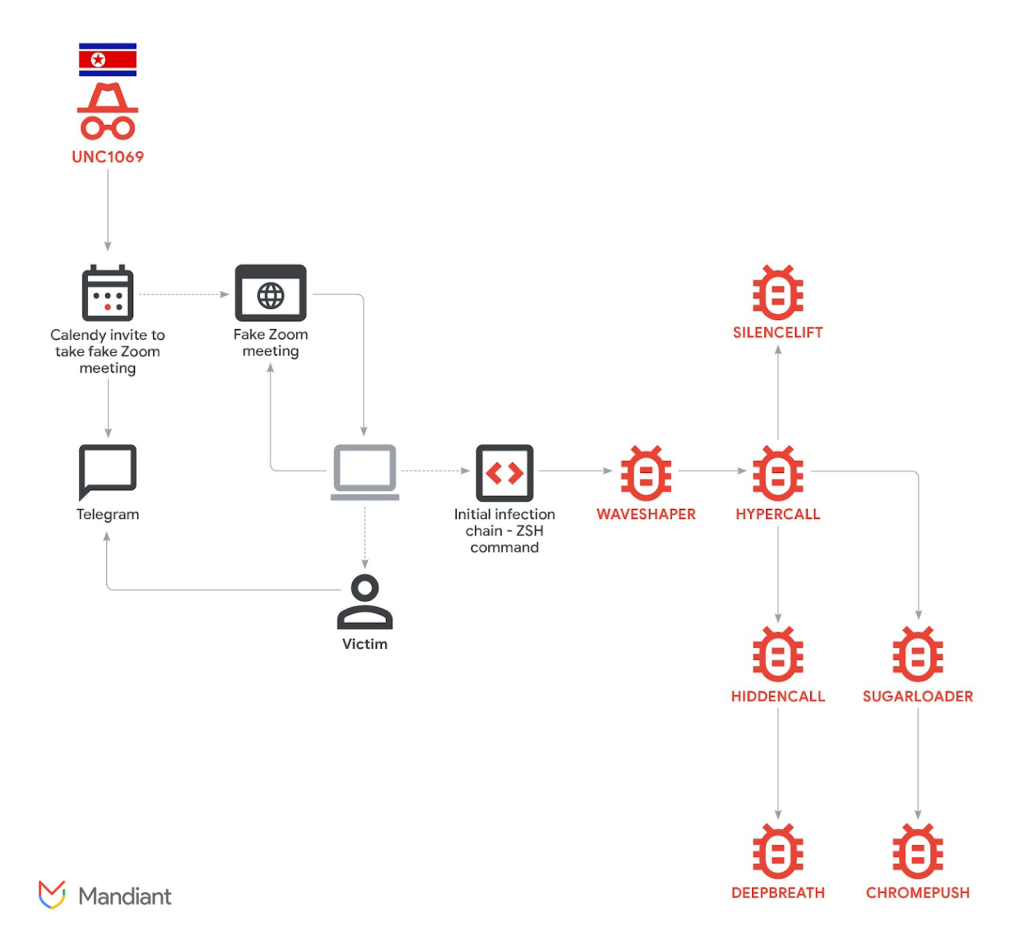
Mandiant noted that SILENCELIFT, DEEPBREATH and CHROMEPUSH are entirely new toolsets for the group. Researchers called it “unusual” to see such a volume of malware deployed on a single host against a single individual.
This suggests a highly tailored operation aimed at extracting the maximum data for two purposes: stealing cryptocurrency and preparing future campaigns by stealing the victim’s identity and contacts.
AI Chrome extensions with malware installed by 300,000 users
Thirty malicious AI-themed Chrome extensions were installed by more than 260,000 users, reported researchers at the LayerX browser security platform.
The campaign masquerades as AI assistants to steal credentials, email contents and information about visited pages.
All analysed extensions appear to be part of a single fraud network, communicating with infrastructure under one domain.
Researchers said the most popular was Gemini AI Sidebar (80,000 users), which has been removed from the store. However, BleepingComputer found that other extensions with thousands of installs remain in Google’s repository:
- AI Sidebar — 70,000 users;
- AI Assistant — 60,000 users;
- ChatGPT Translate — 30,000 users;
- AI GPT — 20,000 users;
- ChatGPT — 20,000 users;
- Google Gemini — 10,000 users.
All 30 extensions share the same internal structure, JavaScript logic and requested permissions. They contain no AI functionality in their code; instead, they load content from a remote domain.
Worse, developers can change an extension’s behaviour at any time on the server side without releasing an update, sidestepping Google’s moderator rechecks.
In the background, the extensions exfiltrate the contents of visited pages, including sensitive authentication pages:
- Gmail surveillance. Fifteen extensions target Google Mail data. A script reads email text directly in the browser and can intercept even drafts;
- data leakage. When using features such as “compose with AI”, the email text is sent to the attackers’ third-party servers, leaving Gmail’s protected boundary;
- eavesdropping. The software also has a speech-recognition function that can be activated remotely. Depending on permissions, it can record the user’s conversations.
BleepingComputer asked Google for comment, but the company had not responded by publication time. Experts recommended checking LayerX’s indicators of compromise, removing the extension immediately and changing passwords.
Connecticut residents charged with stealing $3m
Two Connecticut residents were charged with fraud involving gambling platforms and stolen personal data, the US Department of Justice reported.
According to the indictment, from April 2021 to 2026 the accomplices stole $3m using personal data from roughly 3,000 victims.
The scheme worked as follows:
- buying data. They purchased personal information for thousands of people on darknet markets and via the Telegram messenger;
- account creation. Using the data, they opened thousands of fake accounts on platforms such as FanDuel, DraftKings and BetMGM;
- verification. The defendants subscribed to background-check services (TruthFinder, BeenVerified) to answer knowledge-based authentication questions during account verification;
- automation. One suspect kept a spreadsheet containing victims’ names, dates of birth, addresses, emails and Social Security numbers.
“I was just browsing a list of Social Security numbers and using reverse phone lookup in the Scam Shield app”, wrote defendant Amitoy Kapur in a text message to accomplice Siddharth Lillani.
When details matched, the perpetrator created an account. In some cases, it was possible to proceed without additional checks by BeenVerified.
The aim was to obtain promotional bonuses that bookmakers offer on the first deposit or bet. If such a bet won, the defendants moved the funds to virtual prepaid cards and then to their personal accounts.
Microsoft patched remote code execution in Windows 11 Notepad
Microsoft fixed a critical vulnerability in Notepad for Windows 11 that let attackers launch local or remote programs. They needed only to trick a user into clicking a specially crafted Markdown link, BleepingComputer reported.
With Windows 11, Microsoft dropped WordPad and modernised Notepad, rewriting it from scratch and adding Markdown support. That allowed users to format text and insert clickable links directly in .md files.
According to media reports, the problem lay in improper handling of special elements in commands. A hacker could create a Markdown file with malicious links using protocols such as file:// (path to an executable) or ms-appinstaller:// (app installation).
When opened in early Notepad versions (including 11.2510) in Markdown mode, the text appeared as a link. Pressing it with Ctrl+click caused the software to launch the specified file or protocol automatically. The chief risk was that code executed in the user’s security context with the same privileges, and Windows did not display its standard warning about launching a potentially dangerous file.
Security researchers found it was even possible to link to files on remote network resources. After the patch, clicking any other link triggers a warning dialog in Notepad.
Also on ForkLog:
- Mass delistings strengthened the monopoly of Monero on the dark web.
- The $1m contest winner from X was suspected of multiple rug pulls.
- Eight years in prison and payment of $7.5m: a court sentenced SafeMoon’s former head.
- Experts assessed Russia’s rules for seizing cryptocurrencies.
- The FTX founder accused Joe Biden’s administration of political persecution.
- In South Korea, authorities opened an investigation into Bithumb after a bitcoin “giveaway”.
- Tether froze $544m in illicit funds at Turkey’s request.
What to read this weekend?
In a new ForkLog piece, together with the Mixer.Money bitcoin-mixer team, we examine the consequences of data leaks and how to minimise risks.









